Information Security Risk Management Framework

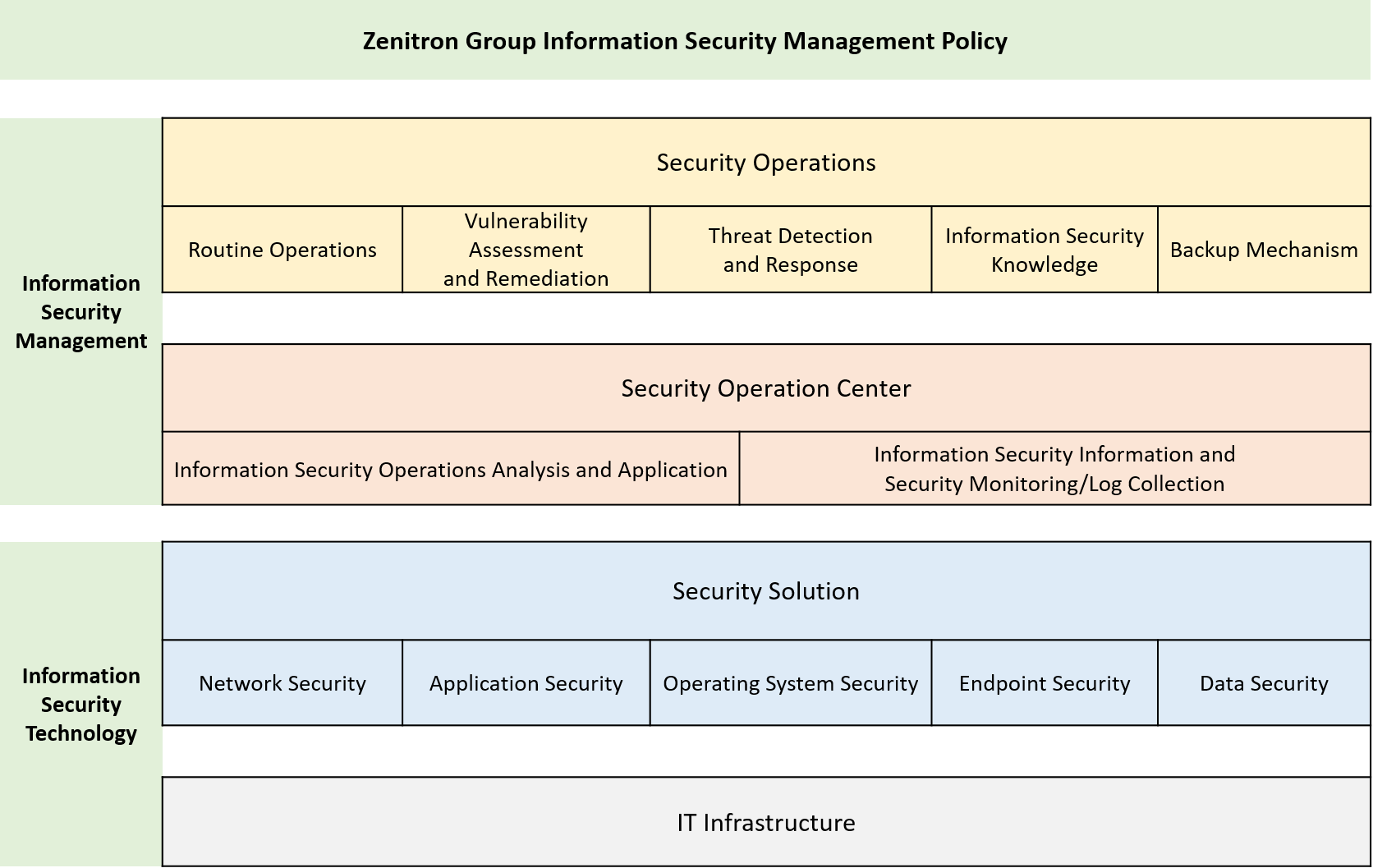
Zenitron's information security is overseen by the MIS Center, which is responsible for executing the information security policies. The personnel involved include the Chief Information Security Officer and at least one Information Security Personnel. They are responsible for promoting information security messages, raising employee awareness of information security, and collecting and improving the performance and effectiveness of the organization's information security management system through technology, products, and procedures.
The Audit Department conducts an annual audit of the internal control system - information system management and information security operations to assess the effectiveness of Zenitron's internal controls over information operations.
In addition, Zenitron's external auditor conducts an annual assessment of the information environment risks based on Zenitron's current information operations and considering factors such as risk management. This includes performing necessary control tests to evaluate the effectiveness of the internal controls over Zenitron's information operations annually.
The Chief Information Security Officer is required to review the information security policies and their implementation annually, and report the findings to the Board of Directors.